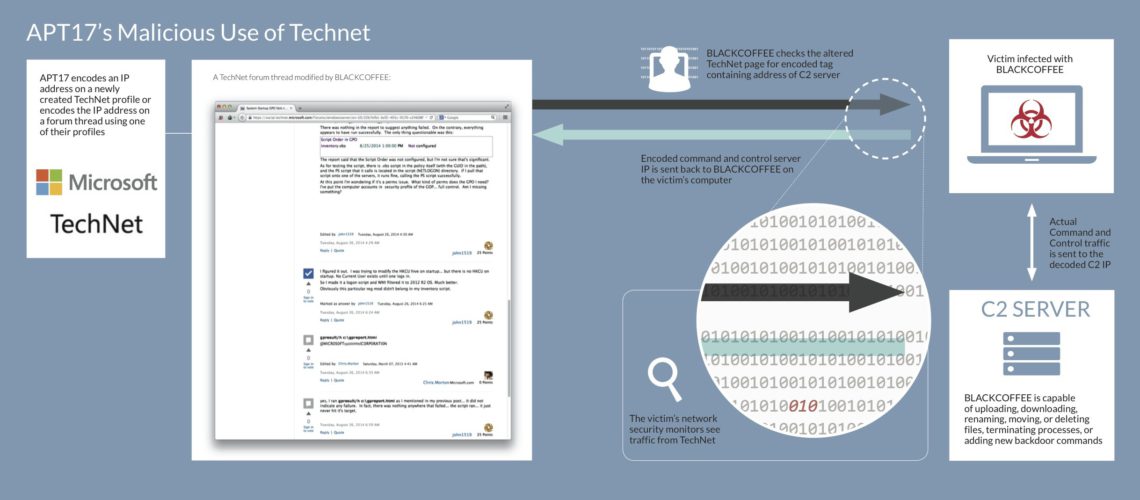
Microsoft’s TechNet portal has been employed by a Chinese advanced persistent threat group in order to hide the IP address of the C&C (command and control) servers of a piece of malware known as BLACKCOFFEE that has been used in cyber-espionage operations.
Strings of the IP address are encrypted and hidden in various threads on the forum, comments or profile pages. After compromising the system, the malware accessed them. This technique is known as “dead drop resolver.”
C&C String Is Hidden Between Certain Markers
Experts with Microsoft Intelligence Center and FireEye analyzed the method in detail. They locked the pages where the IPs were located and sinkholed one of them, which allowed them to observe BLACKCOFFEE’S recent activity.
The attackers are known as APT17 or DeputyDog. The group’s work on different BLACKCOFFEE versions has been found by researchers since 2013. FireEye reports that the crooks’ activities have affected government entities in the U.S., law firms, mining companies, IT companies, and a number of non-government organizations.
How Does BLACKCOFFEE Operate?
As soon as BLACKCOFFEE is installed on a machine, it perform the following operations:
- Exfiltrates data
- Adds new information
- Creates a reverse shell
- Creates a log
- Terminates the running processes
FireEye analysts explain that BLACKCOFFEE includes the links to the TechNet pages that contain the addresses for the command and control server. The numerical string can be found in an encoded form between these two markers: “@MICR0S0FT” and “C0RP0RATI0N.”
As soon as the malware decodes the address, it receives instructions from the C&C server and delivers stolen data.
Same Method Might Be Used by Other Programs
This technique allows the cyber criminals to delay detection of any of the systems employed by the attacker via binary analysis of the threat. In this case, if an infected machine is detected and examined, the operation is not interrupted and the rest the affected computers are still manipulated by the threat authors.
The tactic of hiding the C&C address has been observed in previous cyber-espionage campaigns. Strings of the communication endpoint were detected even on sites like Facebook and Twitter.
FireEye experts warn that other cyber criminals might have already adopted the technique.