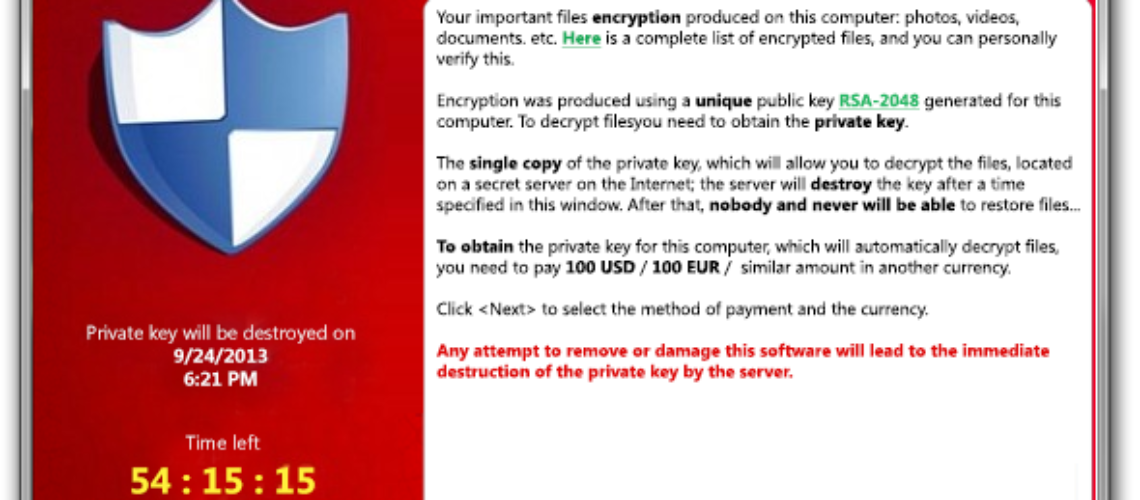
CryptoLocker is probably the most malicious ransomware that has been around since 2013. It targets all Windows versions through asymmetric encryption, leading to the display of a ransom message. Over a relatively short period, CryptoLocker has become a threat of epidemic character. Its latest casualties are found in Australia, as reported by a security firm.
Malware researchers reported that an Australian email security company, MailGuards, has detected a malignant email campaign associating itself with Australia Post. The email consists of information about a parcel being delivered to the victim’s estate, suggesting that a link should be clicked. The link leads to a malicious replica of Australia Post website, looking much like the original one. The attackers also thought of more precautious users and created a second, unsubscribe link within the email.
Once the user is redirected to the attacker’s page, they are downloading a zipped .exe file. Opening the file encrypts the user’s data. The files are not available until the ransom is paid in Bitcoin. The problem is that even if the ransom is paid according to the cyber criminals’ demands, there is no assurance guarantee that the encrypted files may be decrypted.
CryptoLocker’s Encryption Process
As mentioned above, CryptoLocker uses asymmetric encryption, which means that it requires a public and a private key. As already described by malware researchers, CryptoLocker finds the Command & Control server in order to get the public key to encipher the files. Here is a list of the extensions it affects: *.odt, *.ods, *.odp, *.odm, *.odc, *.odb, *.doc, *.docx, *.docm, *.wps, *.xls, *.xlsx, *.xlsm, *.xlsb, *.xlk, *.ppt, *.pptx, *.pptm, *.mdb, *.accdb, *.pst, *.dwg, *.dxf, *.dxg, *.wpd, *.rtf, *.wb2, *.mdf, *.dbf, *.psd, *.pdd, *.pdf, *.eps, *.ai, *.indd, *.cdr, *.jpg, *.jpe, *.jpg, *.dng, *.3fr, *.arw, *.srf, *.sr2, *.bay, *.crw, *.cr2, *.dcr, *.kdc, *.erf, *.mef, *.mrw, *.nef, *.nrw, *.orf, *.raf, *.raw, *.rwl, *.rw2, *.r3d, *.ptx, *.pef, *.srw, *.x3f, *.der, *.cer, *.crt, *.pem, *.pfx, *.p12, *.p7b, *.p7c.
Researchers underline that both businesses and common users are in danger, although business owners are targeted more often. The reason is obvious – attackers demand more money than usually. Any business may be put at huge risk depending on the importance of the encrypted information.
In that relation, MailGuard reveals that different CryptoLocker variants target more Australian companies than before. Business owners should be aware of the danger since experts await a new flood of malicious emails. All employees should be warned not to click suspicious links or links that suggest downloading. Another option is to pay close attention to the URLs of the proposed pages.
No One Is Secure
That is why the most important thing to do is backup your files, especially when you are a business owner. Other options are using a password protection when sharing files, blocking email attachments, and disabling the automatic launching of .exe files.
The positive thing is that the rise of ransomware attacks makes businesses more cautious when it comes to their crucial data.